Use Agentic AI to generate smarter API tests. In minutes. Learn how >>

API Security Testing: Identifying API Security Risks
API security testing helps mitigate security issues for web applications, IoT devices, and other endpoints. Teams can use API security testing to understand complex API behaviors and interactions to identify vulnerabilities that could expose sensitive data.
API Security Testing
What Is API Security Testing?
API security testing is the process of using dynamic application security testing (DAST) and verb fuzzing techniques to identify security misconfigurations and vulnerabilities in an application programming interface (API). The goal is to ensure that APIs adhere to organizational policy and best practices.
In today’s world, APIs are the core part of many applications that power the internet and play a key role in delivering functionality, business functions, and services.
API security testing helps identify where an API diverges from published API specifications. For example, is the API endpoint responding to the correct HTTP requests? This helps validate the correctness of APIs and identify discrepancies in published API specifications.
Ensuring that APIs adhere to published specifications and are protected against malicious inputs and attacks is critical to reducing an organization’s overall security risks. Naturally, API security testing puts a heavy focus on eliminating API vulnerabilities to improve overall application security posture before APIs are deployed to production environments.

Let’s learn more about API best practices, challenges, and key features of API security testing. Automate your application security and API security testing with Parasoft SOAtest to detect and prevent vulnerabilities that may result in cybersecurity breaches.
Want to discover a fresh approach to comprehensive API security testing? Check out our valuable guide.
Benefits of API Security Testing
Security testing for APIs, or application programming interfaces works best when testers incorporate security as part of QA functional testing. Testers can run manual testing and automated tests to enforce security best practices, such as access control with proper authentication and authorization, that all APIs must adhere to in order to pass security scans.
Testers can realize the following benefits in Parasoft’s API security testing solution.
- Identify missing API service method configurations.
- Security compliance and reporting analytics that give real-time awareness of threats associated with your APIs.
- OWASP API Security Top 10 coverage to assist testers in understanding security risks and threats to APIs.
- Proactively identify and detect software security issues in APIs before they are deployed to production environments.
- Shift API security testing into functional testing to reduce the cost associated with finding API security issues later in the testing process.
- QA teams can perform security testing without being security experts.
- Support for multiple OpenAPI formats such as XML, JSON, and YAML.
Automate API security testing in DevSecOps pipeline for continuous feedback on API security issues. These benefits help testing teams improve their DevOps testing efforts and increase visibility into threats that impact their APIs. Realizing these benefits give organizations the confidence they need in deploying API services to support business operations.
Types of API Security Tests
Leveraging SAST and DAST as part of API security testing is the most effective way to test for security issues.
SAST can be used to detect coding issues that present potential API vulnerabilities. Using SAST can help developers improve code quality and security for APIs, as well as ensure things like proper authentication and authorization are implemented correctly in code to fortify APIs.
DAST can be used to perform security testing against your active API assets by running an active test that simulates real-world attacks to find potential vulnerabilities. This includes validating authentication and authorization controls are implemented correctly to protect APIs.
While traditional DAST tools struggle to understand API behavior, Parasoft’s SOAtest + DAST integration can leverage existing API test scenarios to run security testing as part of functional testing.
Other testing capabilities include, but aren’t limited to, the following.
- Functional testing. Reviews API function against specific situations to ensure expected results.
- Fuzz testing. Automated testing that injects invalid, malformed, or unexpected inputs against software to find vulnerabilities.
- Verb fuzzing. A subset of fuzz testing that probes REST endpoints in an attempt to expose sensitive information embedded in APIs. Verb fuzzing scans and enumerates APIs to find weaknesses and vulnerabilities in HTTP services by generating random input through HTTP methods.
Here are just a couple of issues that these API security testing techniques help organizations find. There are more.
- Mass assignment. An active record pattern for web applications can be abused to let users change data components they should not be able to access such as passwords, admin status, or permissions.
- Injection flaws. Users gain access to the shell command, backend database, or OS. Hackers can use this vulnerability to alter, read, or delete data.
API Security Testing Best Practices
Visibility into your API assets is a great starting point to achieve in-depth API security testing. Here’s how Parasoft’s API Security Testing solution helps organizations.
Detect
Effective and comprehensive API security testing starts with detection to find potential security bugs, misconfigurations, and anomalous behavior in your APIs. These issues become blind spots that could expose APIs to attacks. Detection is important to help organizations find and fix security issues early in their SDLC.
Understand
Use your API reporting results to understand your APIs in terms of their value to your business. Use your API coverage data to ensure all API services adequately test for security vulnerabilities. Security testers can use this context to better understand how security threats can impact business logic and behavior of API functionality.
Analyze
Analyzing what changed and how those changes impact your APIs is critical for developing the right set of security tests. Organizations can identify potential attack vectors and exposures that need to be tested for security vulnerabilities. API security testing should provide a continuous approach to analyzing the impact of changes to API resources (authentication, API functions and parameters, data) that help security testers resolve known issues in APIs to ensure effective API security testing.
Launch
Launching security testing and penetration testing as part of functional testing is the ideal way to prevent security vulnerabilities and save in development costs. Finding and remediating security issues in functional testing with a shift-left approach improves the quality and security that enables companies to deploy and implement their APIs with complete confidence.
Examples of API Security Tests
API security testing is designed to find a wide range of security threats and vulnerabilities, like API misuse and abuse, security misconfigurations, authentication, authorization, poor logging, and other issues related to authentication, authorization, and sensitive data.
These threats are documented in the OWASP Top 10 API Security Risks 2023 list and serve as best practices to protect and secure your APIs.
Injection attacks are widely known attack vectors that impact both native web application security and APIs. They occur when hostile inputs are put into an API such as an SQL injection or command injection. These attacks seek to gain privileges in order to gain access to data.
Other examples include something like a test for parameter tampering. This is when someone changes API request values to bypass what should be secure information. Checking related API elements on a web app or website via the browser console is an easy test to tell whether or not an API is secure.
The most common example of an API security test might be input fuzzing. In this test, someone puts random information into an API until something unexpected happens. This can cause error messages or total crashes thus revealing vulnerabilities in an application to outside attackers. It’s important to debug and troubleshoot error messages associated with APIs to understand potential security risks and resolve issues associated with APIs.
The following is a complete list of OWASP API Security Top 10 2023 security threats and vulnerabilities that organizations should be aware of when testing their APIs.
- API1:2023 Broken Object Level Authorization
- API2:2023 Broken Authentication
- API3:2023 Broken Object Property Level Authorization
- API4:2023 Unrestricted Resource Consumption
- API5:2023 Broken Function Level Authorization
- API6:2023 Unrestricted Access to Sensitive Business Flows
- API7:2023 Server Side Request Forgery
- API8:2023 Security Misconfiguration
- API9:2023 Improper Inventory Management
- API10:2023 Unsafe Consumption of APIs
Why Parasoft?
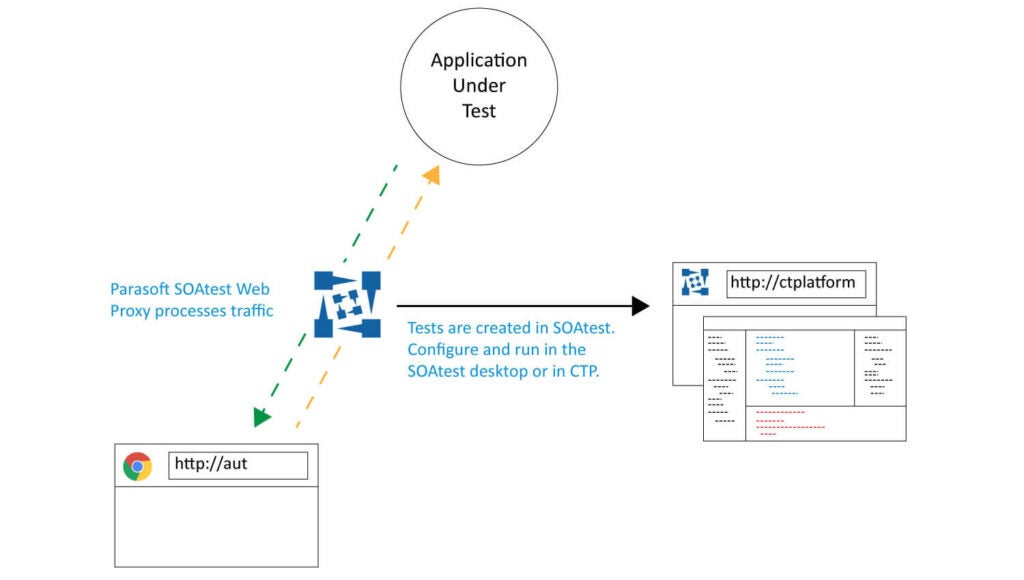
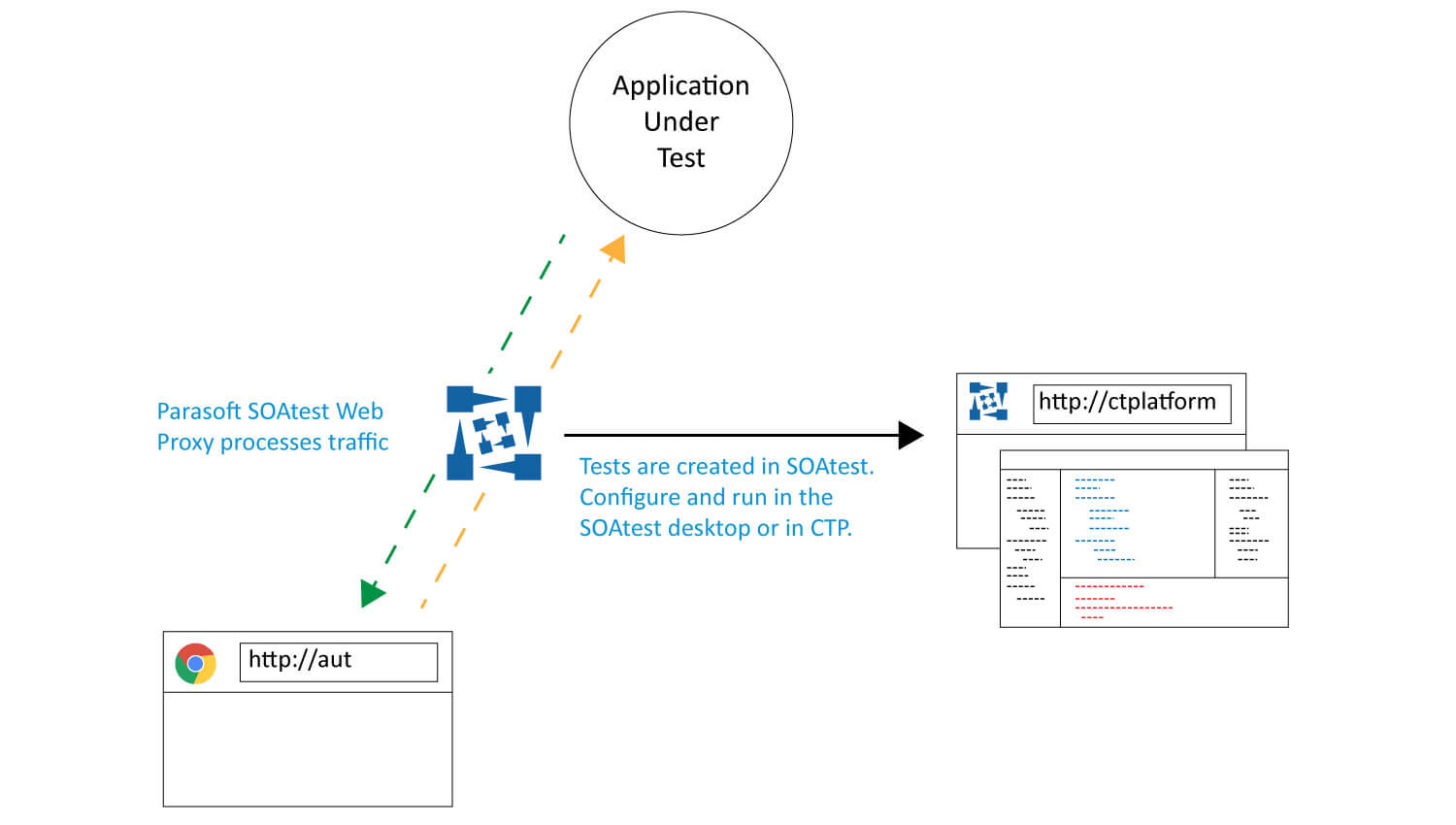
Parasoft converts manual and automated UI tests into automated API tests.
There are many ways to enhance your software development workflow and ensure secure APIs. Automation is one of the few guaranteed measures that will deliver returns.
Whether it’s a CI/CD pipeline implementation, updating best practices for API security testing, or reacting to OWASP API Top 10 changes, Parasoft tools offer agility, consistency, and versatility.
Frequently Asked Questions

Elevate your software testing with Parasoft solutions.