Use Agentic AI to generate smarter API tests. In minutes. Learn how >>
C/C++ Security Testing
Security Testing for Delivering Robust C/C++ Code
Powered by Parasoft’s most complete development testing solution for C and C++
C/C++ Security Testing
C/C++ Security Testing
Users can expertly and efficiently harden their software with Parasoft’s comprehensive security testing solution for C/C++. A comprehensive solution that includes support for cybersecurity standards, and tooling designed to help users tackle the root cause behind software security failures and achieve secure-by-design for today’s connected device software.
How Does It Work?
Parasoft’s static code analysis technology provides high-quality results on the broadest range of security defect types. With over 2500 static analysis rules, Parasoft is able to detect not only security defects in the code, but also pinpoint the root cause engineering issues that led to such vulnerabilities. Reported violations contain metadata that includes severity, stack traces, and parameter values that lead to the reported issue, as well as mitigation advice to fix the code properly. This industry-leading support for static analysis rules and standards fully supports a secure-by-design approach to software development.
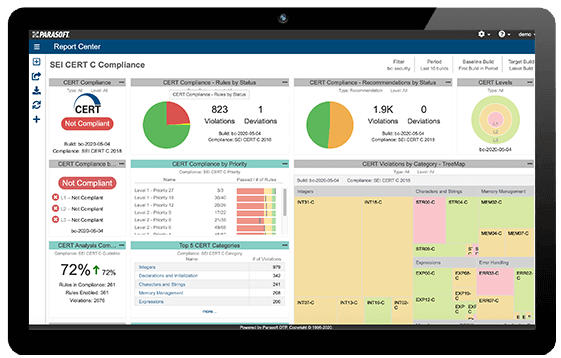
Static analysis security warnings and coding standard violations are reported in a variety of ways depending on the needs of the individual and organization. Developers can get violations reported directly in their IDE where they are working, with full documentation and the ability to repair, suppress, reassign, and defer violations. Managers are given a powerful web interface that provides details in the form of customizable reports, dashboards, historical trends, compliance and audit data, and powerful expandable analytics.
Parasoft has implemented all of the major application security standards, such as SEI CERT C/C++, CWE (Common Weakness Enumeration) coding guidelines, UL 2900, and OWASP, along with security-specific dashboards for each that help users understand risk and prioritization of outstanding violations/vulnerabilities/security defects.
Parasoft has the most comprehensive support for the CERT standard. The Parasoft configuration uses behind-the-scenes data maps that deliver a CERT-centric view, and all violations are reported using CERT identifiers natively. It’s the easiest out-of-the-box configuration available from any SAST vendor. In addition, Parasoft has implemented CERT’s unique set of metadata for each guideline that includes factors used in determining risk and prioritization of static analysis findings, so all violations contain information about the probability of exploit, difficulty, and cost of remediation, and severity if exploited.
Parasoft also supports the CWE coding guidelines. Configurations are available not only for the “Top 25” most common dangerous issues but also for the CWE CUSP. Once a team has mitigated the critical vulnerabilities in the CWE Top 25, the CUSP configuration is a great second step before moving on to the full CWE guidelines. In addition, both the Top 25 and CUSP are core elements of the UL 2900 standard, so complying with them helps prepare products for deployment in an IoT ecosystem.
Parasoft provides CWE-centric dashboards and reports so that violations are reported based on CWE identifiers, making it easy to understand what you’re working on as well as proving compliance to meet necessary regulations. Parasoft leverages data from CWE to help prioritize and categorize SAST findings based on their potential impact downstream.
Parasoft enables you to not only find existing vulnerabilities, but harden your code with solid secure coding standards that reduce the number of CVEs (Common Vulnerabilities and Exposures) in your code/application/device. Analysis can run directly in the developer’s chosen IDE, on a build server, and directly as part of the CI/CD pipeline, giving the developer results when and where the need them while providing management with the necessary understanding to minimize security risk and breeze through security audits.
Features
Benefit from the Parasoft Approach
Move past testing into hardening
Most SAST tools focus on finding potential defects rather than code that could be exploited, filling them with false negatives. Parasoft’s engineering approach prioritizes building security into the application, supported by identifying code that is worrisome and rules for coding best practices. By supporting all of the different models of static analysis, users can move past testing into engineering and truly harden their code against security intrusions.
Know where you stand with security coding standards
Parasoft provides a complete, standard-centric view for understanding where you stand with cybersecurity coding standards. You don’t have to try to map rules to a standard, figure out which findings violated which standard, and then produce a custom report for audits. Instead, you get complete visibility, automatically, to understand which rules you used to meet the standard, which violations were fixed, and which were allowed variance.
Prioritize findings based on cybersecurity research
Parasoft leads the market in implementing application security risk scoring from organizations like CWE and CERT, who focus on issues such as the downstream problems caused by specific violations. Normally a developer would need to understand the importance of, for example, a buffer overflow, and communicate that to management. Instead, users can rely on Parasoft’s technical impact scores that are based not on the code, but on the inherent level of the problem, the likelihood of it being exploited, and the cost to remediate it.
Parasoft C/C++test Resources

C & C++ Continuous Testing

Modernizing Critical Embedded Software

C & C++ Software Testing


Deliver safe, secure, reliable, and compliant C and C++ code with Parasoft C/C++test.