Take a faster, smarter path to AI-driven C/C++ test automation. Discover how >>

Simplify application security testing in development workflows with three simple strategies. Do it early. Do it often. Deploy and deliver confidently.
Application security testing (AST) involves leveraging various testing techniques to improve the quality and security of software applications by identifying, remediating, and ultimately preventing weaknesses and vulnerabilities in all phases of the software development process.
This is a proven way to help prevent cyberattacks. Application security attacks are the most common form of external attack. That’s why improving application security is one of the leading priorities and concerns for security decision makers.
The process of identifying and remediating application vulnerabilities works best when it’s closer to the developer and can be integrated as a part of functional testing. Parasoft AST tools extend automated application security testing across the SDLC to help uncover security and quality issues that could expose security risks in your software applications. This increases collaboration in DevSecOps and provides an effective way for you to identify and manage security risks more confidently.
This includes static application security testing (SAST), penetration testing, using various testing tools, and more. Learn more about the kinds of security vulnerabilities this strategy can mitigate and the tools to improve strategies further. This page also covers DAST and IAST.
Interested in SAST? Check out our whitepaper about how to implement it as a continuous, end-to-end solution that empowers developers to enforce secure coding from the start of development.
Discover how implementing SAST as a continuous, end-to-end solution can empower developers to enforce secure coding from the start of development — and deploy and deliver with confidence at speed.


In order to cover all the bases, testers employ a range of techniques to test their application security. Here are the main ones.
SAST leverages static analysis techniques to analyze source code, byte code, and binaries for coding violations and software weaknesses that expose vulnerabilities in software.
SAST tools provide awareness and feedback to developers about the impact of their coding and refactoring activities in creating vulnerabilities in software.
In contrast, DAST uses black box testing where code is executed then inspected for vulnerabilities.
These tools can often perform more large-scale reviews by simulating ill-natured test cases and unexpected incidents.
IAST combines both DAST and SAST tools in order to provide a more comprehensive list of security weaknesses. These tools dynamically review software while in runtime but operate on an application server. This lets them review compiled code.
IAST tools are great for API testing, as well as reviewing third-party components and data flow.
Uncovering misuse and abuse of API functionality is essential for API security testing. It encompasses the use of DAST and penetration testing activities to find security threats that expose sensitive data embedded in APIs and prevent an API attack.
Finding poorly designed and leaky APIs is important to protect your business, mission, and clients.
Use automated tools in your development processes to improve the software development lifecycle (SDLC).
Integrate AST into your CI/CD pipeline.
Don’t test only UIs and APIs. Also, test interfaces.
Perform simulations to challenge your risk response processes to prevent future data breaches.
Be patient as the teams transform security risk data into actionable insights that can inform future code.
Perform static analysis and dynamic analysis (IAST) to cover your bases with comprehensive software testing.
Utilize a DevSecOps or shift-left strategy.
Use robust test cases that include malicious attacks.
Always review third party or open source components and code.
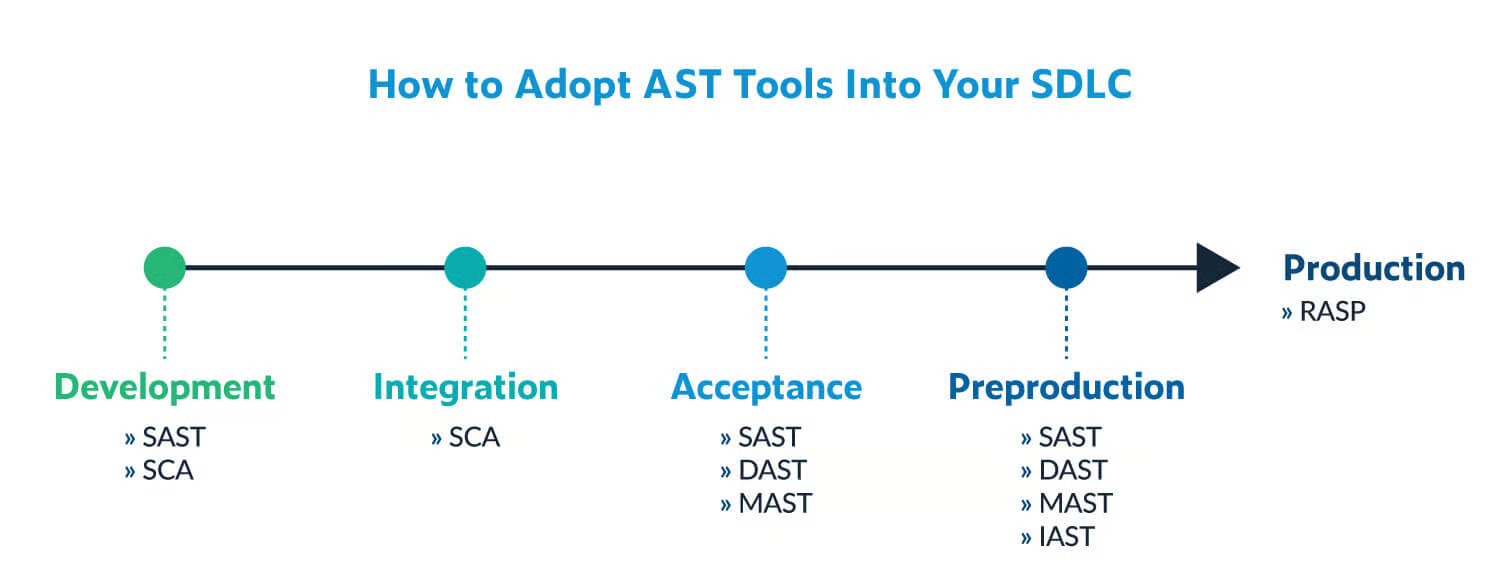
There are many ways to incorporate AST tools into your SDLC. The graphic here shows the recommended application security testing tools to adopt during each stage. But a bigger part of making the most of these tools is automating processes to replace manual testing.
Introducing automation into your development workflow is a natural fit with the shift-left strategy. It also empowers your development team by improving efficiency and productivity and reducing errors. Get started with a Parasoft demo to see how CI/CD pipeline automation might work for your team or how a DevSecOps approach and continuous testing can mitigate security issues.
Chances are there’s a solution for your problem waiting to be discovered.

