Use Agentic AI to generate smarter API tests. In minutes. Learn how >>

DISA ASD STIG
Your software development team can simplify DISA ASD STIG compliance with Parasoft’s industry-leading support across all requirements. From deep application scanning (covering OWASP Top 10, overflows, race conditions, and error handling) to the application of test automation to STIG functional verification requirements.
Designed from the ground up, Parasoft’s solutions are lightweight and containerized to support today’s modern DoD DevSecOps initiatives such as DSOP.
The Defense Information Systems Agency (DISA) provides a variety of Security Technical Implementation Guides (STIG) that give guidance for securely implementing and deploying applications on Department of Defense (DoD) networks. The Application Security and Development (ASD) STIG covers in-house application development and evaluation of third-party applications.
The purpose is stated in the Executive Summary: “These requirements are intended to assist Application Development Program Managers, Application Designers/Developers, Information System Security Managers (ISSMs), Information System Security Officers (ISSOs), and System Administrators (SAs) with configuring and maintaining security controls for their applications.
The ASD STIG uses a severity category code (CAT I, CAT II, & CAT III) to organize and prioritize the guidelines based on the possible impact of an exploit of the particular guideline. CAT I includes the most critical issues for your team to initially place their focus. Most items in the ASD STIG fall in CAT II.
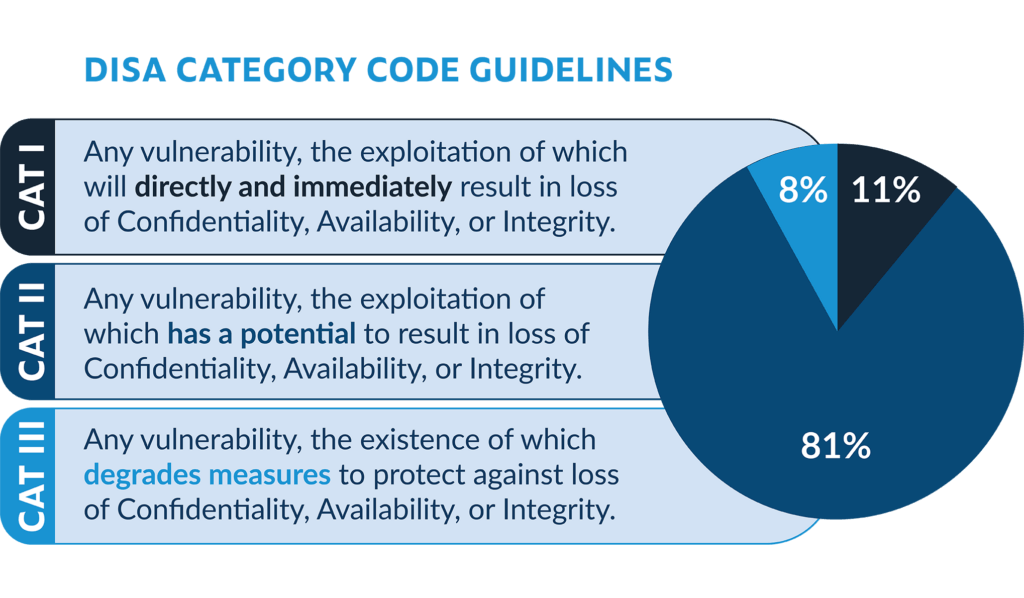
DISA Categories and Distribution by Severity
Compliance with the STIG requirements is evaluated against product and process documentation as well as observing and verifying functionality. These guidelines apply throughout the lifetime of the product from configuration to deployment, maintenance, and end of life.
Parasoft’s test automation tools offer application scanning (penetration testing or DAST), application code scanning (static code analysis or SAST), and other solutions to help validate DISA ASD STIG compliance.
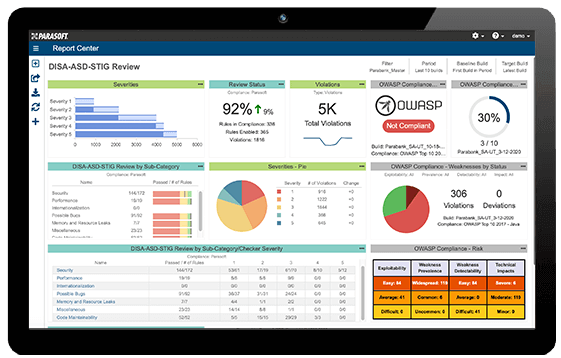
You can achieve DISA ASD STIG compliance with help from Parasoft testing solutions, which identify security flaws required by the standard.
Parasoft static analysis has out-of-the-box support for OWASP Top 10 through preconfigured settings and specific web dashboard reports for C/C++, Java, and C#/.NET. OWASP reporting in Parasoft tools provides a fully auditable compliance framework for projects. These reports are integrated into a standards-specific dashboard like the one in the figure above.
The ASD STIG outlines ways to verify compliance with requirements like application scanning, application code scanning, manual review, and functional security testing. Our tool suite offers application code scanning through static analysis — specifically support the ASD STIG requirement for OWASP Top 10 — as well as buffer overflows, race conditions, and error handling. Using static analysis from the start of development prevents security issues from making their way into the software in the first place.
Verifying API requirements is a key area of test automation that benefits ASD STIG testing. API tests are highly automatable with Parasoft SOAtest. One way to test for this vulnerability is to create a test in SOAtest to examine SOAP messages and verify their time stamps. SOAtest’s penetration testing and fuzzing can generate and run a variety of attack scenarios against your functional test suites.
Code coverage is another important aspect of testing methods listed in the ASD STIG. To get broader visibility into what you’re testing, how well you’re testing it, and how to customize test plans based on priorities, Parasoft DTP captures code coverage metrics from testing frameworks at runtime and by associating coverage with manual tests, automated functional tests, and unit tests.
Parasoft provides a pragmatic approach that emphasizes both STIG validation via static code analysis and preventative techniques to identify and remove vulnerabilities as possible. Automating other STIG rules to the fullest with functional testing tools reduces the tedious manual testing for stigging in the CI/CD for DevSecOps groups.

WHITEPAPER
Download our whitepaper to put Parasoft’s three-level approach into play for efficient, secure, and cost-effective software compliance with DISA ASD STIG.
