Use Agentic AI to generate smarter API tests. In minutes. Learn how >>
Why Automotive Cybersecurity Is Important
Automotive companies now depend on complex software to build smart cars. This has raised some vulnerability concerns in modern automobiles. Read on to learn why automotive companies should integrate cybersecurity into their car development strategies.

Automotive companies now depend on complex software to build smart cars. This has raised some vulnerability concerns in modern automobiles. Read on to learn why automotive companies should integrate cybersecurity into their car development strategies.
The move by many automotive companies to electronic road vehicles has fundamentally changed the industry, increasing the connectivity and smarts in cars. As they become more connected and smarter, electronic vehicles (EVs) also become more reliant on software for vehicle operations, driving more features and functionality to enhance the driving experience.
More features and functionality in road vehicles result in more complexity and more code. More code means more problems.
Problems like an increased vehicle attack surface could lead to vulnerabilities that enable attackers to steal or take control of road vehicles. These problems pose serious safety risks and significant cybersecurity challenges. Such concerns will continue to drive the transformation of modern car design and development.
Since software powers modern road vehicles, cybersecurity is now as important as safety has been in the past. A typical electric vehicle (EV) operates over 100 million lines of code, depending on its equipped features. Protecting road vehicles from cybersecurity threats is more critical than ever before
One of the major attack vectors targeted is the electronic control unit (ECU). It provides vital communication and essential capabilities for operating, monitoring, and configuring the vehicle subsystems.
ECUs are microprocessor-controlled devices that provide a wide range of vehicle essential functions including the following:
The ECUs are grouped into subsystems based on their functionality due to the time-sensitive nature of critical events. Modern road vehicles have up to 100 ECUs running vehicle functions. ECUs primarily communicate via BUS protocols like CAN, LIN, FlexRay, and Ethernet. They also rely on serial, wireless, and optical methods, depending on the application. A gateway manages and validates messages sent by ECUs.
The intention of deploying ECUs behind a gateway is to ensure that only devices that need to communicate with each other are doing so. This is an improvement from traditional ECU designs that accepted commands from and shared information with any entity on the same wiring bus. This was the attack vector for many of the automotive attacks like the famous Jeep hack, which triggered many improvements around automotive cybersecurity standards.
While the gateway remains central for communication and validation, newer trends like domain-based and centralized architectures, Ethernet backbones, and advanced cybersecurity measures are transforming how ECUs communicate. In such architectures, the role of the gateway is evolving to handle high-bandwidth communication, including Ethernet-based traffic, in addition to traditional buses like CAN and LIN. However, as automotive technology advances, the transition toward software-defined vehicles (SDVs) is reshaping the way ECUs operate within modern vehicles.
The proliferation of interconnected ECUs, managing critical functions from engine performance to infotainment, has transformed vehicles into embedded systems networks.
While enabling advanced features, this architecture introduces vulnerabilities in the hardware, firmware, and communication layers. Recent incidents highlight how attackers increasingly target ECUs and their communication protocols, like CAN bus, to compromise vehicle integrity.
A 2024 breach of Kia’s customer portal exposed not only user data but also indirect access to telematics ECUs in connected vehicles. Attackers exploited weak API authentication to send unauthorized commands to vehicles’ head units, potentially altering ECU configurations (for example disabling alarms or geofencing). This incident underscored the risks of insufficiently secured backend systems interfacing with in-vehicle ECUs, prompting Kia to isolate critical ECU communication channels from customer-facing APIs.
Subaru’s Starlink telematics system, which manages OTA updates for safety-critical ECUs (for example, braking and transmission control modules), was found in 2025 to use weak encryption during firmware delivery. Researchers demonstrated that malicious actors could intercept and modify ECU update packages, injecting code to disable collision-avoidance systems. Subaru’s response—adopting cryptographically signed ECU firmware and hardware security modules (HSMs)—illustrates the growing need for end-to-end protection of ECU software pipelines.
In late 2024, thieves exploited vulnerabilities in adaptive headlight control ECUs, which were improperly isolated from the vehicle’s CAN bus. By physically accessing the headlight wiring, attackers sent spoofed CAN messages to the powertrain ECU, bypassing immobilizers and enabling keyless theft. This attack emphasized the importance of segmenting noncritical ECUs (such as lighting systems) from safety-critical networks and implementing CAN bus intrusion detection systems (IDS).
The 2025 Pwn2Own Automotive competition showcased escalating ECU-focused exploits. Participants targeted:
These demonstrations accelerated industry adoption of ECU-specific protections, such as runtime integrity checks and secure debug interfaces.
Modern vehicles rely on 100+ ECUs, creating a sprawling attack surface. Recent breaches highlight three priorities:
Regulatory frameworks like UN R155 now mandate ECU-specific risk assessments, while standards like ISO 21434 require ECU lifecycle security controls. As vehicles evolve, safeguarding ECUs, and the networks connecting them, will remain pivotal to mitigating cyber-physical risks.
Building security-in from the onset is the number one goal of the new automotive cybersecurity standard, ISO 21434. There’s a running tally of vulnerabilities in ECUs that demonstrate the seriousness of cybersecurity and its impact on safety, which this standard attempts to address with requirements and recommendations that directly impact how components for road vehicles are designed and developed.
ISO 21434 seeks to integrate high-quality safety and cybersecurity measures throughout the entire product engineering lifecycle to ensure road vehicles have been designed, manufactured, and deployed with security mechanisms to protect the confidence, integrity, availability, and authenticity of vehicle functions in road vehicles.
Two core aspects of ISO 21434 focus on the following.
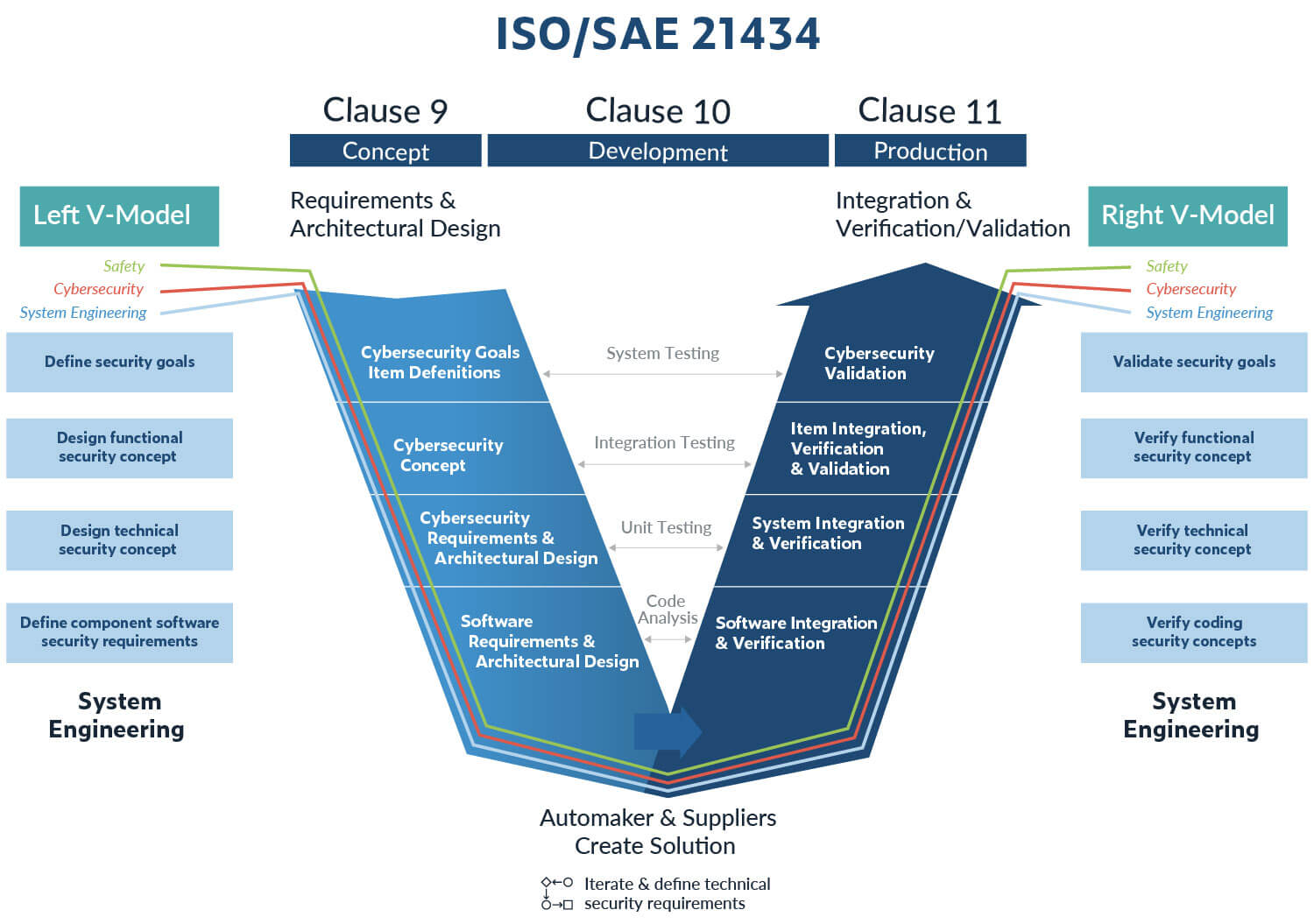
Software testing plays a critical role in helping manufacturers and suppliers address requirements and recommendations outlined in ISO 21434. Formalizing static code analysis as part of software verification activities is an ideal way to identify and eliminate ambiguity in code, as well as pinpoint weaknesses that could expose vulnerabilities in software used in ECU components. This helps minimize the attack surface that an attacker can exploit to compromise ECUs that control critical vehicle operations.
Specifically, ISO 21434 references and calls out static analysis in section 10.4 Requirements and Recommendations.
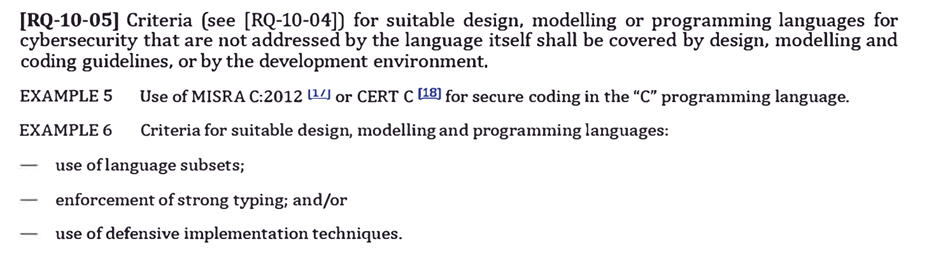
The requirement details section 10.4.1 for design highlights the need to select programming languages suitable for enforcing code that’s syntactically correct with valid structure and grammar. The code must logically make sense semantically and correspond to a set of rules for the language being used. Code must be able to compile cleanly to transform into a sequence of instructions.
Enforcing strong typing, the use of language subsets, and implementing defensive implementation techniques are all requirements specified in ISO 21434. Formalizing secure coding compliance practices using Parasoft MISRA C/C++ and CERT C/++ checkers and rules will help manufacturers and suppliers adhere to ISO 21434 requirements and recommendations for mitigating potential risks in software and design.
Employing cybersecurity and safety coding practices to support software verification and validation is a best practice and essential in confirming the cybersecurity specification outlined in ISO 21434. Using Parasoft C/C++ code analysis capabilities eases the rigor of software testing associated with critical-safety software.
Automating software testing with Parasoft C/C++test and C/C++test CT is made simple with an integrated approach that incorporates AI-enhanced static analysis, code coverage, unit testing, requirement traceability, and reporting analytics to streamline your ISO 21434 compliance requirements.
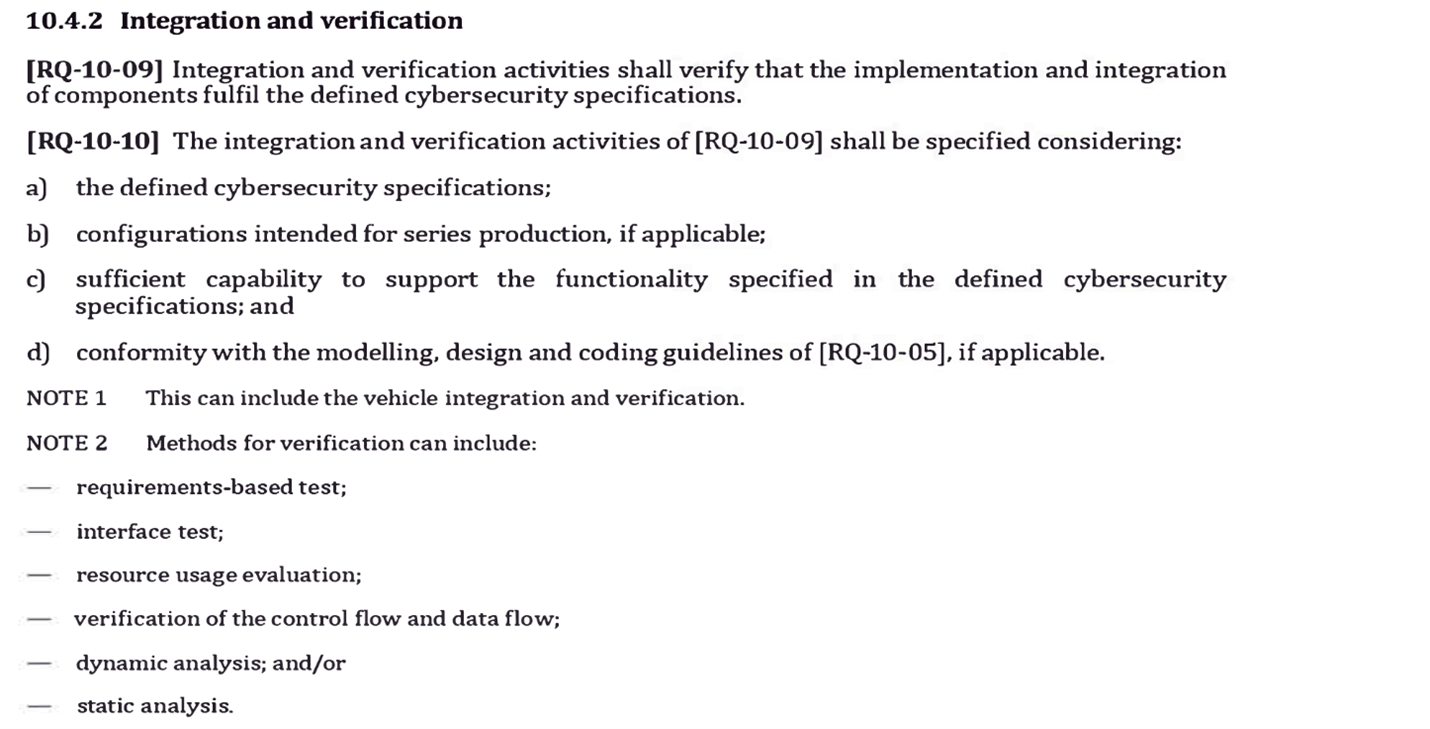
ISO 21434 section 10.4.2 provides a list of methods for software verification that can be satisfied using Parasoft’s C/C++ code analysis capabilities. Many security bugs can be detected using control and data flow analysis. Parasoft’s C/C++ code analysis engine is primed to give product engineering teams the breadth and depth into complex flow analysis like use-after-frees, double frees, and buffer overflows.
Other software verification and testing activities referenced in ISO 21434 include fuzzing, penetration testing, vulnerability scanning. They’re listed as recommendations, noted by RC-10-12. Given the complexity and size of modern software development, running additional testing techniques and tools should be required because each technique finds different types of issues.

To uncover security risks in software product engineering teams should use tools and testing techniques to cover the following scenarios.
Putting cybersecurity in the front seat of road vehicles with ISO 21434 will help the automotive industry drive better practices to reduce and mitigate cyber threats and attacks that could eventually lead to fatalities.
The connectivity and intelligence in cars has changed the way cybersecurity is contextualized and prioritized in product engineering. By formalizing ISO 21434, product engineering teams can leverage threat analysis and threat modeling activities to inform design decisions and product development throughout the entire lifecycle.
Building security-in cannot just be a catchy phrase anymore because drivers’ safety and security is at stake. Cybersecurity must be ingrained into the entire product engineering team mindset and activities so that the entire team is thinking about ways in which software should be designed and developed to prevent and mitigate cyberattacks.
ISO 21434 provides a road map to help manufacturers and suppliers navigate through safety and cybersecurity challenges in product development. This new standard serves as a building block to bolster security protection mechanisms in road vehicles that will ultimately save lives.
Parasoft’s C/C++ integrated automated testing solutions are the best of breed and scale across your SDLC and product engineering efforts. Uniquely positioned with deep experience and expertise in the embedded software market, Parasoft helps you meet your safety and cybersecurity compliance needs.

A unique combination of software test automation tools, analytics, AI, and reporting provides visibility into quality and security issues from the start. This enables product engineer teams to accelerate software verification in accordance with standards and best practices required by the marketplace.
"MISRA", "MISRA C" and the triangle logo are registered trademarks of The MISRA Consortium Limited. ©The MISRA Consortium Limited, 2021. All rights reserved.